Top Ten Content Management Systems
Introduction
Content management systems can bring a world of difference to the Internet. Reading content, which the web is filled with, can be nearly impossible without a CMS. CMS or content management systems power many of the websites that you use on a daily basis. Whether you are checking the news or reading your favorite blog, chances are that some website that you use each and every day is using a content management system.
Top Ten Content Management Systems
10. Expression Engine
Expression Engine is a great contenet management system for those who are designers and web professionals. Expression Engine has a large amount of flexibility that lets it be molded into whatever use is conducive to its owners. Best of all, Expression Engine has a built in cache function that can help the busiests websites sustin themselves during high traffic periods.
9. Drupal
Drupal is an open source, completely free CMS. This means that users do not have to worry about paying to deal with their content management system. Drupal also has thousands of add-on modules and is able to create any site that you desire. The modules and add-ons are a stunnign way to increase your ability to mold the sites that you would like in the future.
8. Joomla
Joomla is unique in the fact that it wants its users to succeed. Joomla is developed through an open source initiative that gives more effort towards wanting their users to know what is going on with the project. Even if you are not an expert, you are encouraged to get involved in Joomla and help it to become the best content management system out there. Best of all, feedback costs nothing!
7. Concrete Five
Concrete Five lets users who are not super technically experienced create amazing websites. You do not have to be on the top of the world to realize that a lot can be done with Concrete Five. Drag and drop functionality as well as the free cost brings Concrete Five in at number seven in our countdown.
6. Cushy CMS
Cushy CMS is another user friendly non-technical CMS. It is currently deployed to over 10,000 websites that are live and being displayed on the Internet right now. Users are able to safely and easily download and upload content as well as make edits to content on their installations. Cushy CMS is safe for those who are not experienced and want to try a CMS out for the first time. Cushy CMS also does not cost anything.
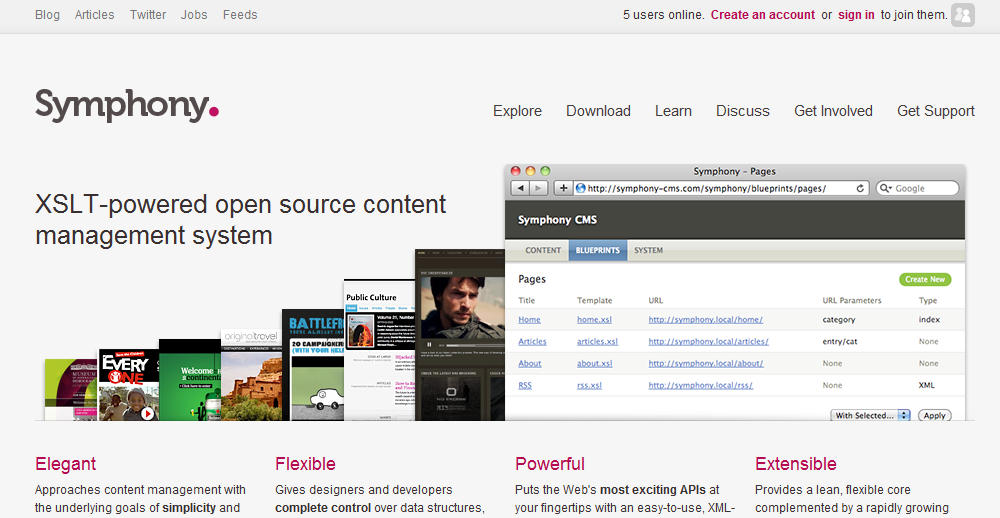
5. Symphony
Symphony is a CMS designed for developers. Anyone who enjoys going in and digging around with code will love using this content management system. However, there are a lot of people who do not like doing so. Symphony is versatile and easy to use for developers but might not be the first choice for those that are not as technically inclined.
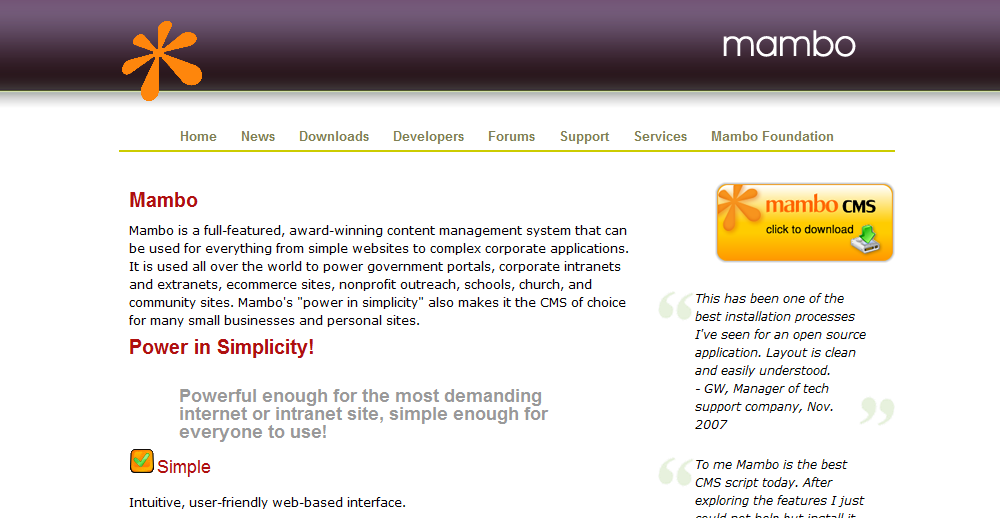
4. Mambo
Mambo is very well known to developers and users of CMS. Mambo has the ability to be complex as well as very simple. It is up to the user how complex they want to take the system. Don’t worry if you don’t know much. Mambo is hosted on sourceforge, one of the largest open source development communities in the world.
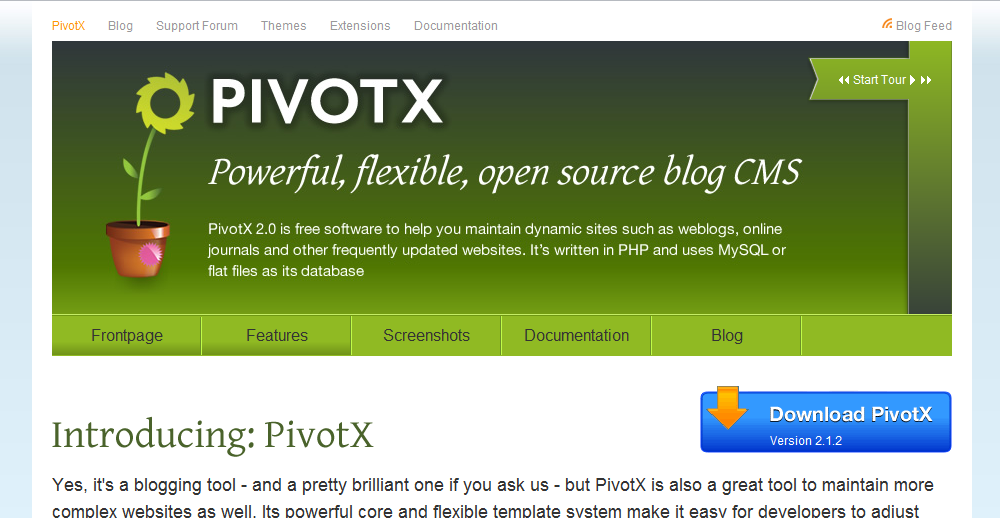
3. PivotX
PivotX is an easy to use open source blog CMS. It is great for any type of site you are building regardless of how simple or complex it is.
2. Railfrog
Railfrog is built on top of Ruby on Rails. This is the same powerful software application that has Twitter and Basecamp as some of its sister websites. Railfrog does require that developers know a little bit about how to use and code Ruby on Rails. However, they provide excellent information and are willing to work with anyone who does not have all of the necessary experience to work with Ruby on Rails.
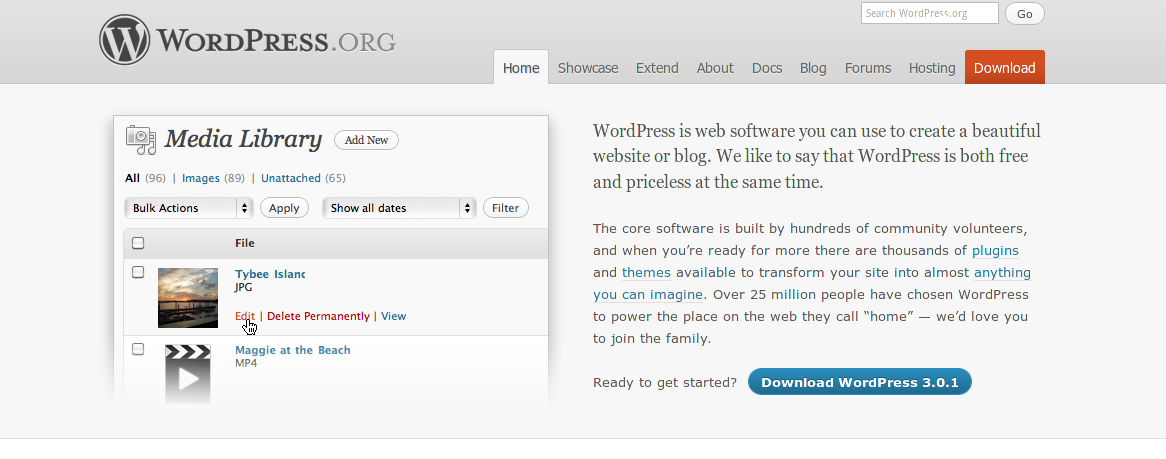
1. WordPress
WordPress is an amazing blogging software! While it is first thought of as a blogging software, the software in WordPress can be used to create websites and manage loads of content as well. WordPress is used on over 10% of the Internet today. Check out where you can use WordPress and how you can use WordPress by looking at their websites along with the codex for all of the developer support that is necessary.
There is a content management system for almost everything. Whether you have found the perfect CMS or not, you have learned a large amount about what a CMS can do for your web presence. What is your favorite CMS? Please share in the comments.
Introduction to Linux: Basic Terms and Helpful Hints
Linux is a wide ranging installation that can be difficult for some individuals to understand. When you take a look at all of the different tips, tricks and how to’s that must be learned in Linux, it can be daunting. That is why it is much easier to break apart Linux into smaller parts.
A Kernel is at the heart of Linux. Kernels are the part of Linux that makes the operating system work. Linux kernels are often customized to meet the exact needs that an individual has for their uses of their personal computer. Distrobution is a variant of Linux. Fedora, Ubuntu and other distrobutions are able to be downloaded by users and posted up to the Internet. Linux distrobutions may also be downloaded as Live CDs for users who want to try a certain distrobution before installing it on their computer. Terminals are the location for the entrance of commands. Terminal commands are useful for customizing the Linux distrobution as well as allowing users to change a vast majority of their distrobution.
 Mounting is the process where you bring up a certain part of a hard drive or other resource. Partitions are portions of the hard drive that are setup to be virtually walled off. Linux users also need to know about the shell. This is an overlaying portion of your computer where it is the outer shell of what needs to be run in order for the computer to work. The home user will be the first user created on your Linux installation. All documents, photos, videos and other data will be stored under the home folder on the installation. Each and every user you create on the machine will have a folder where their data will be stored. Becoming a superuser is necessary from time to time. Simply open up the terminal command box and type in sudo as a prefix to whatever command you need to run. This will enable you to complete the command using temporary superuser access. Package managers allow you to dowload new programs. Think of these as an iTunes for your programs on your computer. Most programs are free and some may already be installed within your distrobution.
Mounting is the process where you bring up a certain part of a hard drive or other resource. Partitions are portions of the hard drive that are setup to be virtually walled off. Linux users also need to know about the shell. This is an overlaying portion of your computer where it is the outer shell of what needs to be run in order for the computer to work. The home user will be the first user created on your Linux installation. All documents, photos, videos and other data will be stored under the home folder on the installation. Each and every user you create on the machine will have a folder where their data will be stored. Becoming a superuser is necessary from time to time. Simply open up the terminal command box and type in sudo as a prefix to whatever command you need to run. This will enable you to complete the command using temporary superuser access. Package managers allow you to dowload new programs. Think of these as an iTunes for your programs on your computer. Most programs are free and some may already be installed within your distrobution.
Troubleshooting on Linux computers can be a little difficult for the untrained eye. It is worth checking to see if your graphics card has Linux drivers that are available to download. Users should consider installing these drivers if they are available. Ubuntu is one of the easiest systems to reset. It can be reset to the recovery mode and have the entire graphics user interface reset, a common source of problems for users. Ask around! The linux community is well known for being able to help new users or users who simply have a question about a problem that they cannot solve. Do not be afraid to reach out and ask a question to someone.
Wine is a great resource for helping users to find compatability solutions for programs that run in Windows. You may be able to find a way to run your World of Warcraft or other program on Linux by using one of the tools that Wine makes available. Check into it to see if you can use Wine instead of having to deal with a dual booting situation. The main reason that so many people enjoy using Linux is that it is logical, simple, fast and easy to use. There are so many more steps that individuals can take to enjoy the programs that they are working with in Linux. Are you going to join the world of Linux today?
Linux is one of the fastest growing development areas on the Internet today. Many programs that are installed on Linux distrobutions including Open Office and GIMP have been ported over to the Windows OS. Users of Linux need to be aware that they will have to learn about how to use the terminal, kernel and other functions if they are not fully trained in how to use them. However, that does not mean that they will have to spend years learning it. Once learned, Linux is a great operating system to use in any IT environment.
Don’t Be a Victim. Protect your PC from Viruses and Malware
Introduction
Computer infections are becoming a more common problem every single day. Users have to deal with the problems of having a Trojan horse, malware infection, spyware infection or a virus infecting their personal or business computer. However, computer infections do not have to be a daily part of your life. There are many excellent computer security programs that can help even the novice user to ensure that their computer is protected from the widest range of threats possible.
Trend Micro Titanium

The Trend Micro Titanium family of products has a lot to offer users. There are various levels of virus protection as well as the ability to ensure that you will be protected from malware, spyware and some of the products even include the ability to utilize parental controls. Trend Micro Titanium is the most recent release of the Trend Micro Internet Security product that has been produced for years. Users of Trend Micro benefit from a user friendly software program that will allow them to stay safe while using the Internet. Trend Micro Titanium runs anywhere from $40 to $80 depending upon the exact version that is selected.
Norton

Norton Anti-Virus 2011 is one portion of the suite of products that is offered by Norton’s parent company, Symantec. Individuals who have ever used Norton Anti-Virus know what the program can do in order to keep problems out of your computer. Often, problems may be spotted within your computer and Norton will be one of the first Anti-Virus programs to notify you. It is vital that you take a look at all of the different programs that are offered under the Norton name. First, you have Norton Anti-Virus 2011 with Anti-Spyware. This program offers a basic level of protection. Norton Internet Security 2011 takes things to the next level. Once you have Norton Internet Security 2011, parental controls, smart firewall and identity protection are all included to protect you. Norton 360 provides 360 degree online protection from any Internet maladies. Right now, Norton 360 is available for the exact same price as Norton Internet Security 2011 and both can be installed on up to three computers within your home. Ensure that your computer meets the minimum required specifications before installing Norton onto it. Norton has been known to take up a large amount of processor power and memory usage on older computers.
McAfee

McAfee Internet Security and McAfee Total Protection are two additional programs that are available to home users who need protection against viruses, spyware and other intrusions entering their computer. It is vital that you know what is going on within your computer so that you are not going to have dozens of infections that are transmitting your bank account password, your checking account number or other vital information to other criminal elements. While there is only a five dollar price difference between McAfee Internet Security and McAfee Total Protection, it is well worth the extra small amount of money to ensure that you have the best protection possible. McAfee Total Protection has extra phishing protection that the more affordable version of the product does not offer. Also, your home network is protected from outside intruders along with the fact that your valuable files will be secured using McAfee Anti-Theft.
Malware Bytes

Malware Bytes is a useful program for individuals who encounter a large amount of malware, spyware and other non-virus infections on a regular basis. While this program does not offer the real time detection without a paid upgrade, it does an excellent job of removing infections that have eaten into your computer once they occur. Infections that cause your computer to have adware, spyware, malware or a combination of anything from the above are able to be removed without a problem thanks to Malware Bytes. Also, the quick scan that is included with Malware Bytes is able to detect the most common problems in a matter of ten to fifteen minutes. This is an entire “quick scan” of your computer! However, do not worry. When there are any additional problems encountered in the detailed scan, they are just as easy to remove. You simply hit the removal button and all of the infections are removed as quickly as possible. Sometimes a simple restart may be required in order to succeed in the complete removal of the infection.
As you can see there are plenty of free tools available to keep your PC safe from people and software with malicious intent. While this is not a complete list it is a great start for someone needing to get inexpensive but effective virus protection. Please feel free to share your favorite virus, spyware, and malware tools in the comments.
How to Safely Surf in a Hacker’s Paradise
Introduction
Many individuals do not bat an eye when they see that their restaurant, dry cleaners or even favorite hair salon is offering free wireless Internet. Most consumers expect that the wifi is their god given right, just as anything else would be. However, this can be dangerous once the users of the connection realize that they are not surfing safely nor securely.
Common Problems Among Wifi Users
 The first step in ensuring that you surf the Internet both safely and securely is to have the connection established securely. Do not connect to an open network that you do not know. Computer hackers or other scam artists could have setup the connection to entice you to connect and login to something with vital details. An account such as your bank account, credit card or even your retirement account could become compromised due to a connection on an insecure router. Exposed data can be used to create identity theft problems or even expose individuals to fraud.
The first step in ensuring that you surf the Internet both safely and securely is to have the connection established securely. Do not connect to an open network that you do not know. Computer hackers or other scam artists could have setup the connection to entice you to connect and login to something with vital details. An account such as your bank account, credit card or even your retirement account could become compromised due to a connection on an insecure router. Exposed data can be used to create identity theft problems or even expose individuals to fraud.
Protecting your laptop might seem like an easy step after how badly your Internet could be affected. However, most individuals do not think to make sure that their laptop is protected. Having an up to date anti-virus program as well as a firewall will ensure that the bad individuals who want to compromise your computer are not able to attack it. Do not leave your shared folders enabled when you are using a wifi hot spot or public wifi connection. Anyone who wishes will be able to see your shared folders and access them at will. This could expose all of your private data and cause serious problems to individuals who leave critical data in these areas.
Solutions
SSL or secure socket layer is a great tool to use when browsing websites that you do not want to share details about. All of this information passes through an extra layer of security and cannot be accessed without the proper authorization. It is very difficult to access the account of anyone who uses a public wifi connection with SSL enabled on the website they are browsing. SSL is offered by most banks, financial services and many other websites. Take advantage of the service if it is offered to you.
 A virtual private network connection or VPN is a great tool to surf securely. While you are going to connect through the hot spot you are not going to be stuck surfing on the hot spot connection entirely. When using a VPN you are actually attaching to an external network. This network then will allow you to go out and allow you to browse. The network that you are connected to locally will serve as an encryption tool.
A virtual private network connection or VPN is a great tool to surf securely. While you are going to connect through the hot spot you are not going to be stuck surfing on the hot spot connection entirely. When using a VPN you are actually attaching to an external network. This network then will allow you to go out and allow you to browse. The network that you are connected to locally will serve as an encryption tool.
An encrypted hot spot is the best possible prevention tool to surf safely when using public wifi. An encrypted hot spot cannot be accessed unless an individual allows it. You will not be able to have your data stolen and the entire connection is protected. T-Mobile is one of the many companies that are currently using encrypted hot spot technology within all of their hot spots.
Folders, Credit Cards and More!
 Your data is one of the main items that you are going to want to protect on your computer. No one wants their data to fall into the wrong hands. That is why you should be focusing on securing your folders and other data areas of your computer so that they cannot be accessed. The easiest method to go about securing your data when using public wifi is to select the public option in Windows XP, Vista and 7. Anyone who selects this option will automatically have the option to share their folders turned off within Windows.
Your data is one of the main items that you are going to want to protect on your computer. No one wants their data to fall into the wrong hands. That is why you should be focusing on securing your folders and other data areas of your computer so that they cannot be accessed. The easiest method to go about securing your data when using public wifi is to select the public option in Windows XP, Vista and 7. Anyone who selects this option will automatically have the option to share their folders turned off within Windows.
Watch for an expired SSL certificate or no SSL certificate when entering your credit card information should it be a paid connection to the Internet. That way you will have the best connection possible and ensure that it is not another site trying to get your credit card information. Keep your computer up to date to ensure that you are protected from all the threats on the Internet today. Also, ask the business if they actually have a hot spot or if they are being taken along. You may just be surprised and they may be too! Ask questions before it is too late and you will be able to safely surf using public wifi.
How do you keep you PC safe when using a public hotspot? Please feel free to share your opinions and tips in the comments.
10 Questions to Prepare for and Ace any Interview
Interviews are one portion of the working world that many people would rather avoid. Many individuals are nervous whenever they enter an interview situation. Preparing for the top interview questions allows those nervous feelings to be put at bay and avoid freezing up when a manager or interviewer asks you a question.
Interview Questions
1. What is your greatest weakness?
Few people want to admit that they have a weakness that could lead to their downfall. Give your greatest weakness but play it off with a strength. Also, tell what you are going to do to improve your greatest weakness. You should always be striving to fix any weakness that you have so that you will be a better overall person.
2. Why should we hire you?
What sets you apart from the crowd of people apply for jobs these days. Are you different because you have a skill set that is important to the business? Explain in a short and concise answer what you would do differently that would make you a better candidate than other candidates on the market. Focus on positives in this answer.
3. How would you describe yourself?
 Think of words that describe you and why you pick them. Explain your choices and ensure that they are real characteristics about yourself. Thinking about yourself might seem difficult or awkward. Don’t forget that there are other people who are going to work with you each and everyday. They will know if you are lying, so just be truthful about who you are and what you are like.
Think of words that describe you and why you pick them. Explain your choices and ensure that they are real characteristics about yourself. Thinking about yourself might seem difficult or awkward. Don’t forget that there are other people who are going to work with you each and everyday. They will know if you are lying, so just be truthful about who you are and what you are like.
4. Where do you see yourself in five years?
Have a set of goals that make sure you are looking forward to the future. There are so many goals that people simply do not think of that are obvious. Having a higher salary, living a better life or even moving into a home are all goals that are honest. Make sure you have a goal set for something in your professional life. This could mean rising through the ranks or any number of different goals that you could set based upon your profession.
5. Why do you want to work here?
Do not say “I need a job”. Employers will see you as someone who simply wants a paycheck and does not want to contribute to their organization. While not every company will have a strong culture, some companies will want you to focus on helping them to improve more than others. Think about what the real motivation is behind you wanting to work somewhere. It could be due to benefits, pay, corporate culture or another reason.
6. How would you deal with a customer who is angry?
 This question is common to receive in a retail setting or another customer service position. You must be careful to not further irritate the customer and solve the customers problem. Companies want to see individuals who are able to be cool under pressure as well as give customers real solutions. A simple answer to this question is stating that you would apologize to the customer, give them realistic options and consult with your manager or supervisor for additional solutions should the solutions available to you be unsatisfactory.
This question is common to receive in a retail setting or another customer service position. You must be careful to not further irritate the customer and solve the customers problem. Companies want to see individuals who are able to be cool under pressure as well as give customers real solutions. A simple answer to this question is stating that you would apologize to the customer, give them realistic options and consult with your manager or supervisor for additional solutions should the solutions available to you be unsatisfactory.
7. When were you most satisfied with your last position?
This question is meant to determine your goals. Job seekers need to understand when and why they were satisfied with their last job. This can be a difficult question due to so many experiences. Common answers include when you first joined the company and when you left. If possible, think of an answer involving your time in the middle. Group problem solving and teamwork are great situations to talk about with satisfaction in previous jobs!
8. What salary are you seeking?
Don’t give out the number you are seeking without asking the employer what they typically give someone with your experience. The employer usually will give you a salary range. Ask for whatever pay you believe you deserve within that range. Make sure that you backup your argument.
9. Are you a team player?
Everyone says yes to this question but you must back up your answer with some realistic facts. Don’t say that you are a team player if you don’t have anything to back it up. Examples can include work projects, collaboration across departments and other similar situations. 9
10. Do you have any questions for us?
 Do not ask about salary at this time! You should ask about job qualifications, why the position was vacant and other questions that will show that you have a high level of interest. This will help to prepare you with all of the information you need to be successful.
Do not ask about salary at this time! You should ask about job qualifications, why the position was vacant and other questions that will show that you have a high level of interest. This will help to prepare you with all of the information you need to be successful.
There are so many interview questions that can be asked. While most individuals cannot choose the questions that they are going to be asked, they can prepare for the most common questions to ensure that they will be ready when they are asked some of the most common questions.
Please feel free to share your interview tips and advice in the comments.
LAN Protocols – All You Need to Know
LAN protocols are one of the most frequently used and talked about IT tools. Whether you work for a company that specializes in medical research or a company that is focused on furniture manufacturing, LAN protocols make a big difference in your day to day working environments. 802.11 is the spectrum that is used by most LAN networks.
WLAN Networks
 802.11a is a format of wireless local area network that never really developed. The sequence eventually progressed in the WLAN field from 802.11b to 802.11g to 802.11n. The 802.11n flavor of WLAN is the newest and fastest supported WLAN standard. Speeds on a 802.11n network can reach up to 110 MBPS. This is one of the fastest supported yet and will become even faster once more optimizations and upgrades are done over the next few years. The WLAN support fields operate off of the 5 GHZ frequency spectrum. WLAN protocols are constantly changing. It takes just two to three years before the next generation of the 802.11 networks will be up and running in a draft configuration. While this might seem like a long time, it goes by extremely quickly.
802.11a is a format of wireless local area network that never really developed. The sequence eventually progressed in the WLAN field from 802.11b to 802.11g to 802.11n. The 802.11n flavor of WLAN is the newest and fastest supported WLAN standard. Speeds on a 802.11n network can reach up to 110 MBPS. This is one of the fastest supported yet and will become even faster once more optimizations and upgrades are done over the next few years. The WLAN support fields operate off of the 5 GHZ frequency spectrum. WLAN protocols are constantly changing. It takes just two to three years before the next generation of the 802.11 networks will be up and running in a draft configuration. While this might seem like a long time, it goes by extremely quickly.
Networks switching
Most LAN protocols are switching over to WLAN. Companies are able to save space, wires, staff time as well as money switching to WLAN. There is less infrastructure to maintain and the office does not have to be rewired each time someone needs to change the configuration of their cubicle or office space. Best of all, the entire office is covered by the network instead of specific networks drops within the entire space of the office.
LAN Network Technology
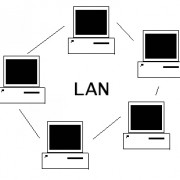 LAN protocols that are based upon traditional wired networks typically use CSMA/CD technology. This method of networking has the network devices such as a desktop workstation or laptop connect to printers, projectors and other network media. Busier networks will not be able to use this technology as network devices cannot send information at the same time. When a collision of data occurs, the two devices will time out for a randomized amount of time before attempting to resend their data. This is one reason why larger networks simply do not utilize this technology. However, in smaller offices it is useful as it is not nearly as difficult to setup and collisions do not occur often.
LAN protocols that are based upon traditional wired networks typically use CSMA/CD technology. This method of networking has the network devices such as a desktop workstation or laptop connect to printers, projectors and other network media. Busier networks will not be able to use this technology as network devices cannot send information at the same time. When a collision of data occurs, the two devices will time out for a randomized amount of time before attempting to resend their data. This is one reason why larger networks simply do not utilize this technology. However, in smaller offices it is useful as it is not nearly as difficult to setup and collisions do not occur often.
Token Passing
A token passing network requires that the device have a special token before it can transmit data. One device at a time can have the token and the token cannot be shared with more than one device. Once one device has transmitted its data, the next device will receive the token. Delays are smaller than the CSMA/CD technology as well as easier to predict in length. Token passing still does not allow for full network utilization but is much more useful on larger networks.
When you are trying to utilize LAN protocols, understanding LAN is a large part of it. Do not forget how the difference LAN protocols work and which technology is the best for your network.
Top 10 MUSTS for Tomorrow’s Wireless Security
Wireless security has become more important than ever. While there used to be few people who used wireless routers or wireless Internet access, the amount of wireless Internet access has climbed exponentially recently. Ensuring that routers are secured and that hackers/crackers cannot access your connection can protect you from having your personal security compromised and being accused of crimes.
Encryption
Whether you are the average joe or a sophisticated hacker, one must ensure that they have some form of encryption on their router. The most common types of encryption include WEP, WPA, WPA-2. While the other formats were fine for earlier routers and times, every router should now be protected by a WPA-2 level encryption. This is a much more secure encryption format and will make it more difficult for anyone to crack your password for the router.
Password
 Many individuals forget to set a secure password for their router. Setting a secure encryption level but not setting a secure password will ensure that your wireless security flies out the window. A password should be at least 14 characters, alpha numeric with symbols included. The more confusing and difficult you can make your password, the better it will become. However, do not forget to write down your password so that you can continue to access the router in the future.
Many individuals forget to set a secure password for their router. Setting a secure encryption level but not setting a secure password will ensure that your wireless security flies out the window. A password should be at least 14 characters, alpha numeric with symbols included. The more confusing and difficult you can make your password, the better it will become. However, do not forget to write down your password so that you can continue to access the router in the future.
SSID
Broadcasting the routers SSID may encourage individuals to try to gain access to your Internet connection. There is no need to broadcast the SSID of your router. Simply write down the SSID and turn off the public broadcasting of your SSID. Not only will your connection remain secure, individuals will be able to connect without having the constant search for the correct connection.
Mac Address Filtering
Mac address filtering will ensure that your wireless security is protected for years down the road. Each and every device that connects to the Internet has its own MAC address. This is a device specific address that will allow the device to be identified. Connecting to your router’s configuration settings and changing the MAC address will ensure that you can block out all other devices and only allow the computers that you wish to connect to the network. This can come in handy if your neighbors decide that they want to download the entire library of movies over your Internet connection.
 Disable Wireless Access to Your Router
Disable Wireless Access to Your Router
Many individuals attempt to gain access to a router through web access and change the settings within the router. Disabling wireless access to the router will help to ensure that your wireless security will remain secure for years down the road. Administrators can still change settings and other tools by using the Ethernet cable to connect to the router and change settings.
Change the Default Router Password
Saving the same default router password such as “password” or “default” or “administrator” is a great way for users to change the settings you worked hard to create. Change the password to a different password than your encryption password. This will ensure that your connection remains secure and that potential trouble makers do not have access to the tools that they need to wreak their havoc.
Turn on the Firewall
Many routers may have a firewall to keep out some of the unwanted traffic. While you do not have to turn on the firewall, it may help to keep out some of the traffic that does not belong. Think about whether you want to turn the firewall on or off before doing so. That way you can be successful at keeping your wireless security as strong as possible.
Update Your Computer
Computers that are connected to the network need to be patched and repaired to the best of an individuals ability. Not having a protected computer can allow for many different types of files to access your system. There is no reason to have an infection of any type reach your computer. Plan ahead and allow for your computer to be secured by installing an anti-virus program as well as updating with any patches that are released for your operating system.
 Have as Few Routers as Possible
Have as Few Routers as Possible
Some individuals find it fun or amusing to install extra routers for better signal strength or simply to be useful to them. However, unless these routers are secured and patched as well as properly passworded/encrypted they will be useless in helping your Internet/wireless security situation. Make sure that any extra access points are following the rules that should be followed with any router on a wireless network.
Turn off DHCP
DHCP is a process that can ruin your wireless security. Turn it off as soon as possible. Assigning a static IP address to each computer within the network is faster than having to secure the network again due to some stupid mistake that was made. DHCP is simply not a good idea at this modern time.
Whether you already have implemented some of these ideas or none of these ideas, secure your Internet today. There is no reason that you should not have a secured connection as soon as possible! A secured connection for tomorrow’s wireless security will ensure that your personal information is secured and that your Internet is only used for what you want to use it for.